Introduction
In an era where digital infrastructure forms the backbone of our daily operations, the threat of Distributed Denial of Service (DDoS) attacks looms larger than ever. These attacks, growing in both frequency and sophistication, pose a significant challenge to traditional security measures. This article explores how Graph Neural Networks (GNNs), a specialized artificial neural network can revolutionize the way we detect and combat DDoS attacks.
What are Graph Neural Networks (GNN)?
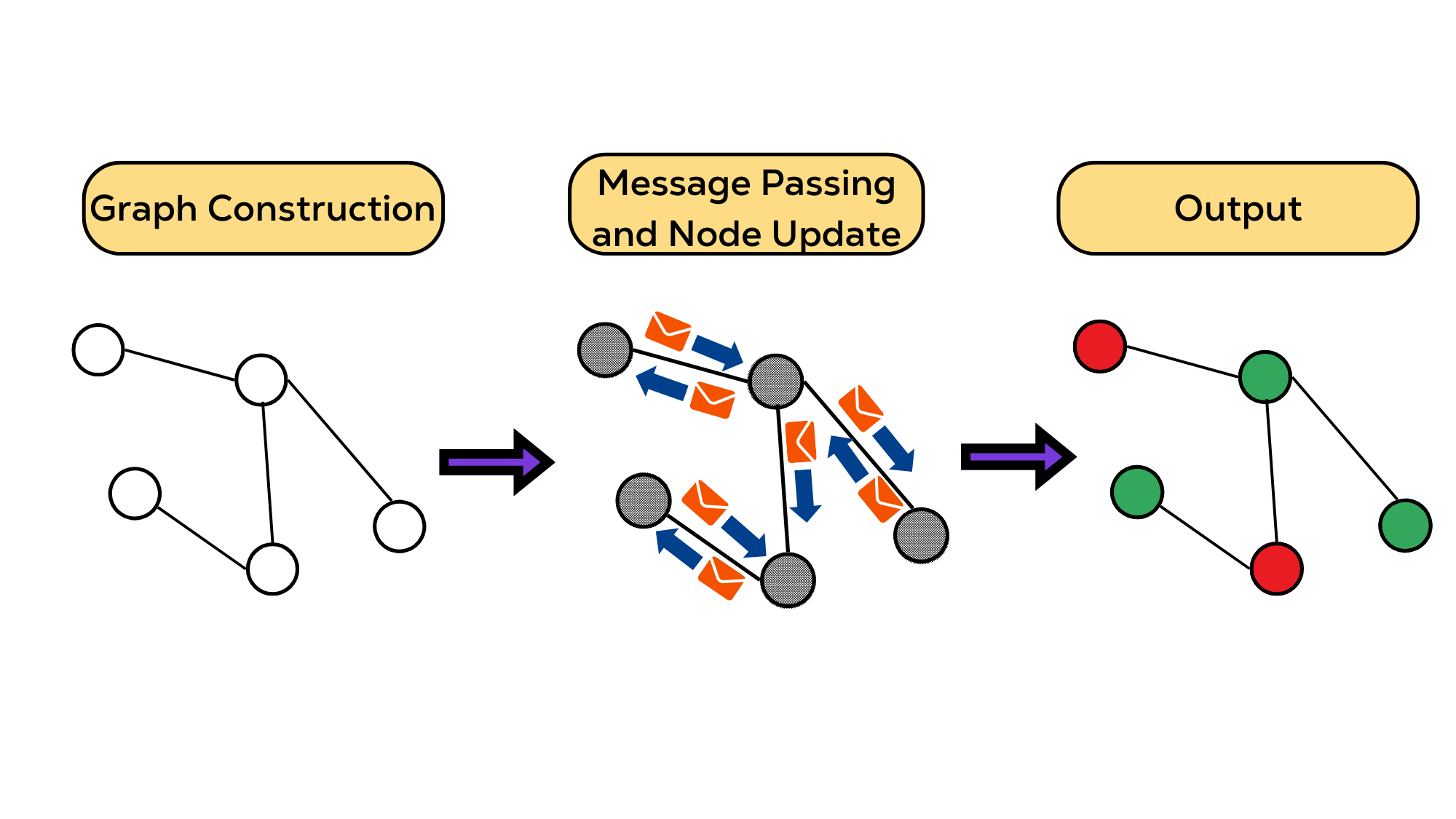
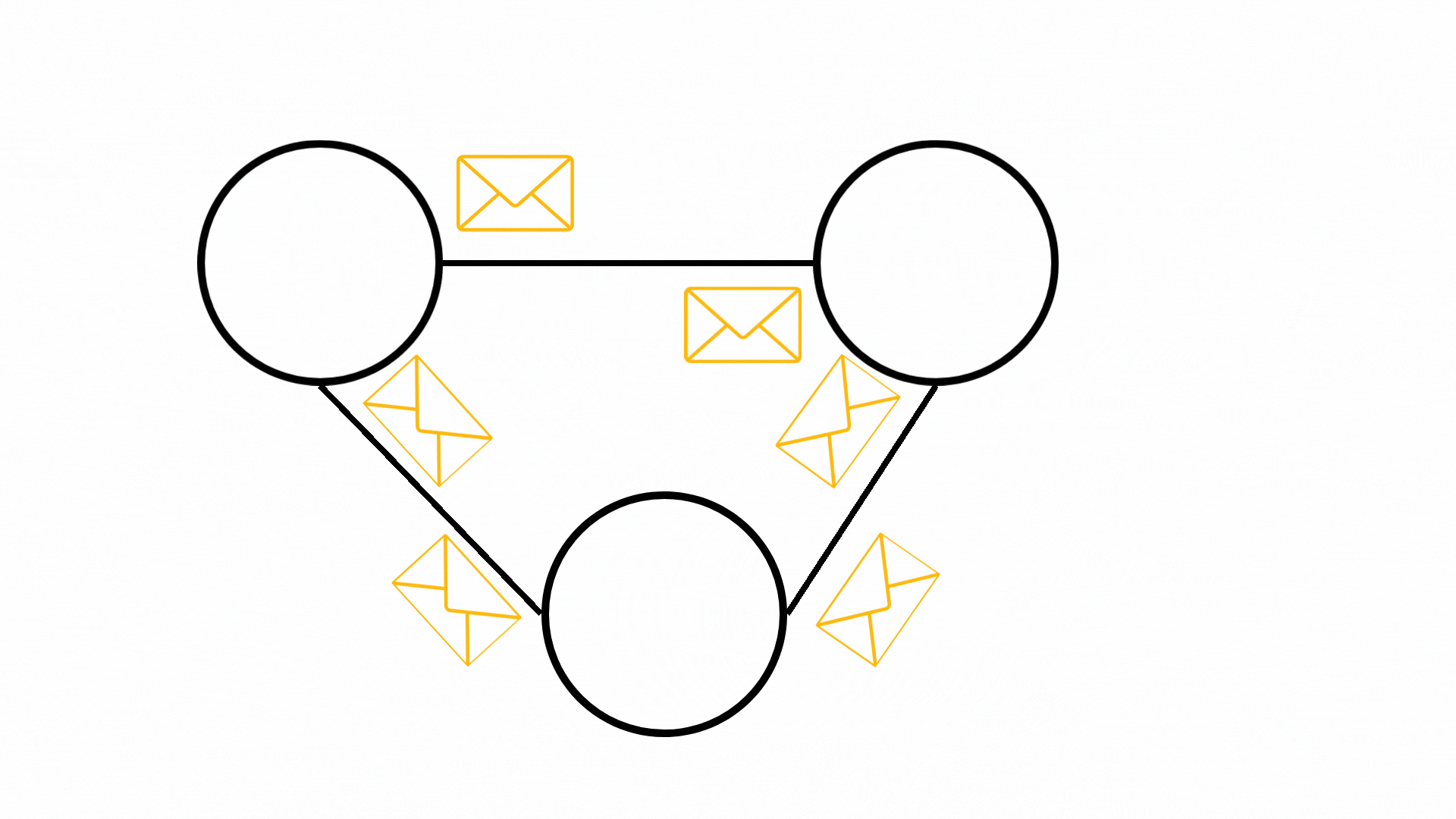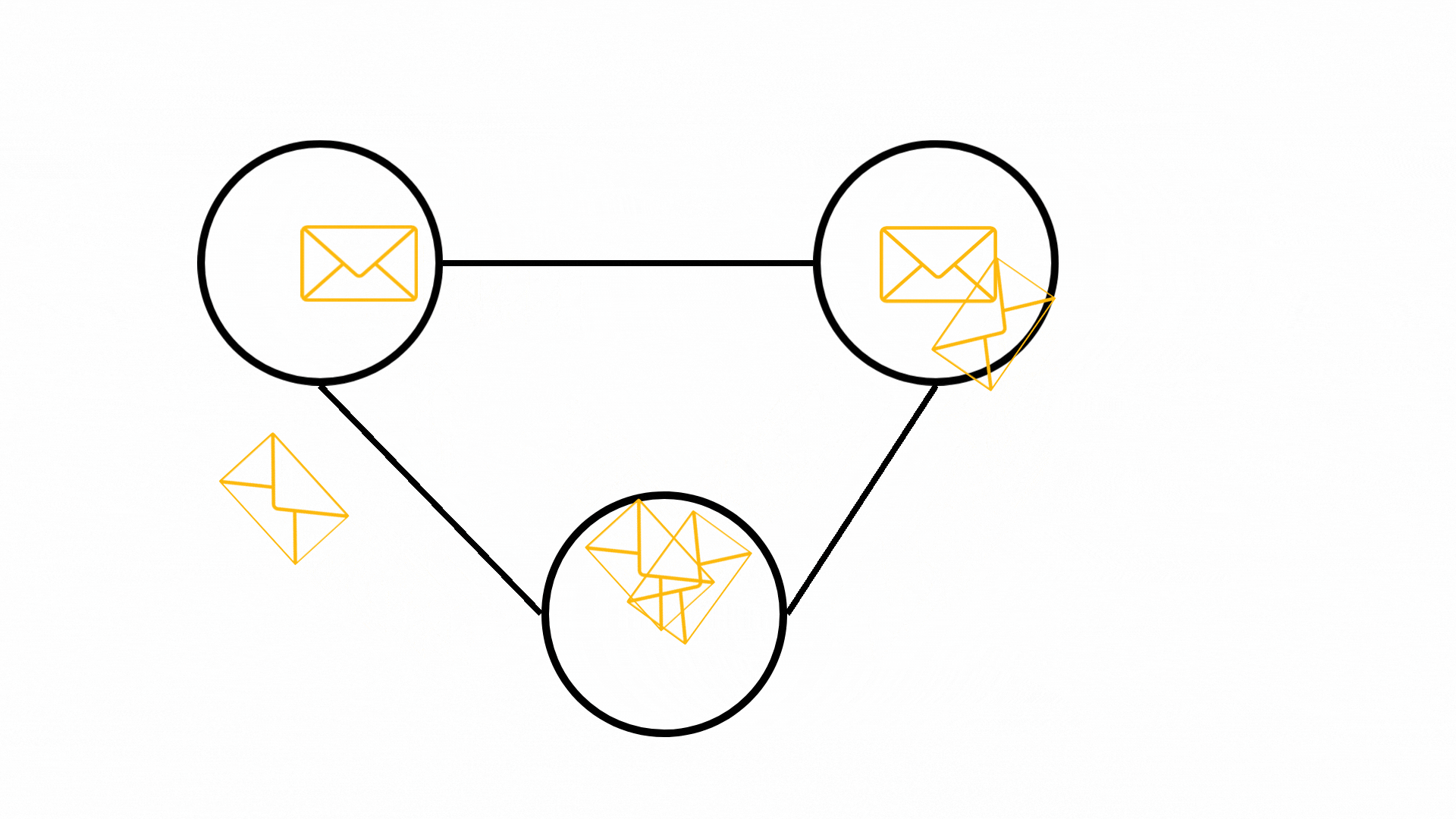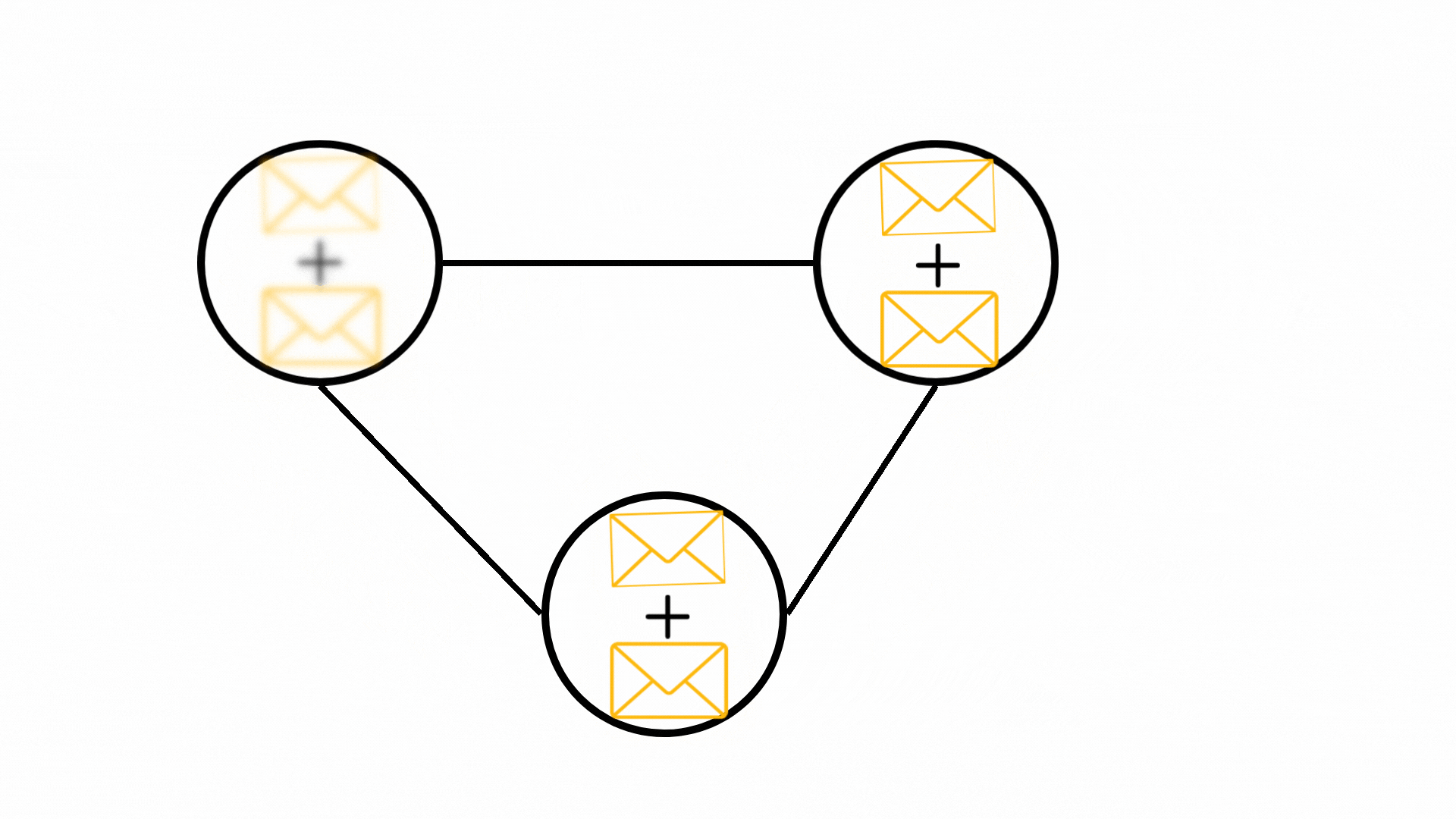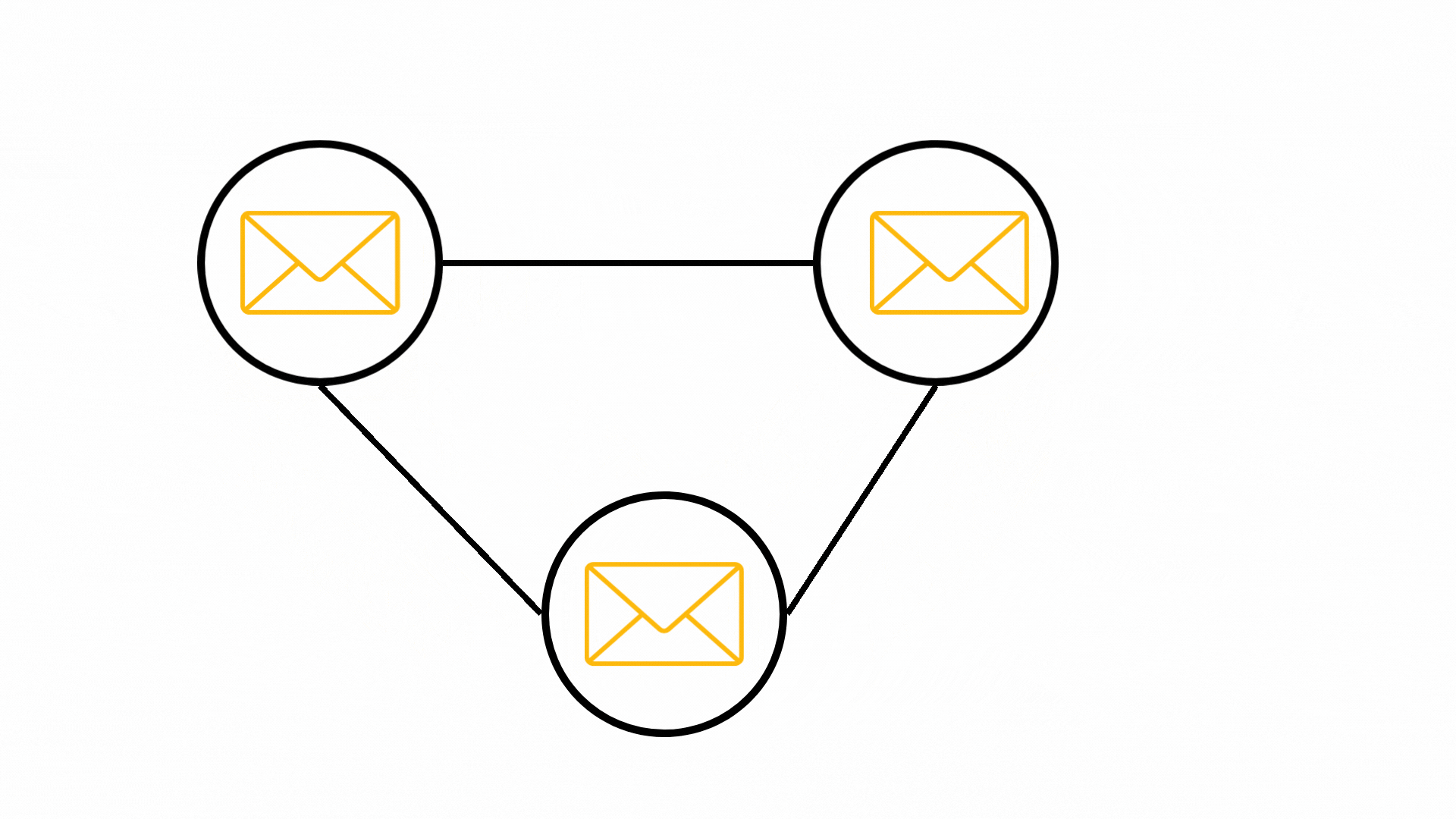
Figure 1: Basic structure of a Graph Neural Network showing Graph Construction, Message Passing & Node Update, and Output.
Graph Neural Networks (GNNs) represent a breakthrough in artificial intelligence, specifically designed to learn and generalize from graph-structured data. Unlike traditional neural networks that process fixed-format data like images or text, GNNs excel at understanding and analyzing interconnected information systems - making them particularly valuable for network security applications.
At the heart of modern GNNs lies the Message-Passing Neural Network (MPNN) framework, which provides the foundation for most state-of-the-art GNN models. Let's break down how this system works:
Graph Structure
The network operates on a graph
$G=(V,E)$
where
- $V$ represents the set of nodes (vertices)
- $E$ represents the connections (edges) between nodes
Each node starts with initial features that encode its starting state. These features are transformed into a hidden state vector that will evolve through the learning process.
The Message-Passing Phase
The magic of GNNs happens during the message-passing phase, which occurs in several iterations:
Message Creation
- Each node communicates with its neighbors by passing messages which are nothing but its current hidden state. Sometimes the current hidden states are inputed through a neural network to create a message.
Message Aggregation
- Nodes collect and aggregate messages from their neighbors.
- A special aggregation function combines these messages and ensures consistent output regardless of how many neighbors a node has.
State Update
- Each node updates its hidden state based on:
- Its current state
- The aggregated messages from neighbors
- This update can be performed using a simple aggregation function or with another neural network function.
The Readout Phase
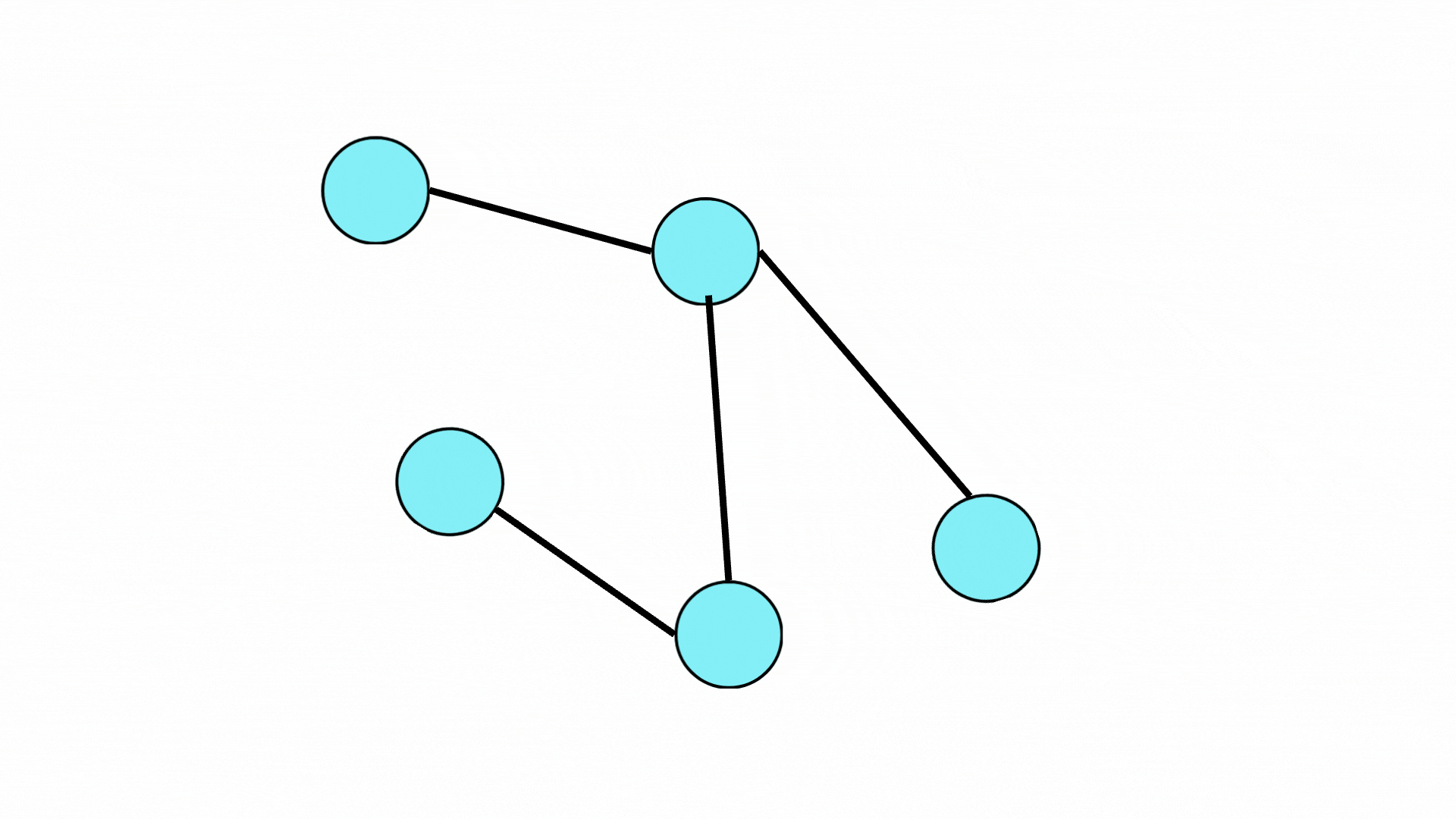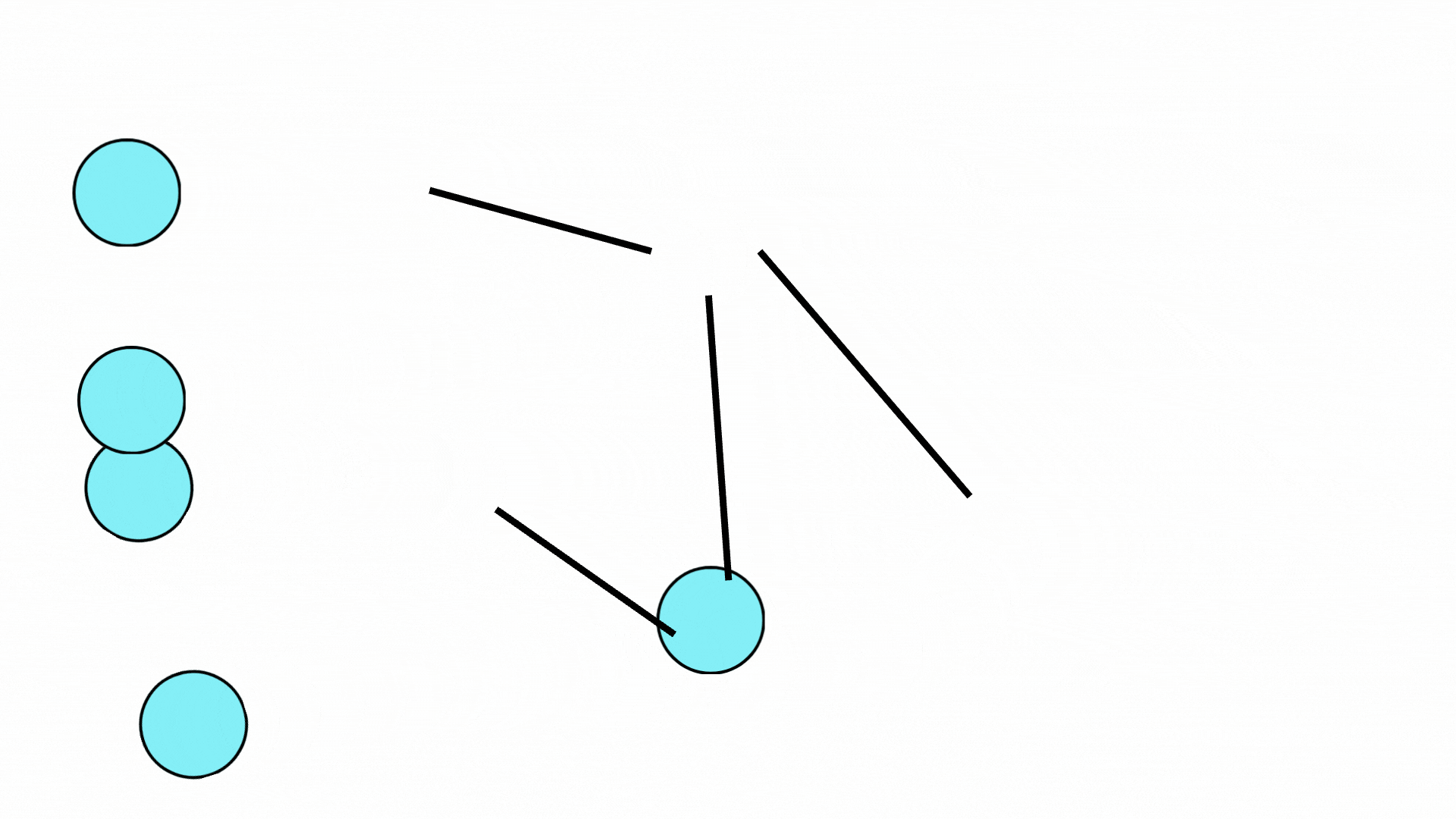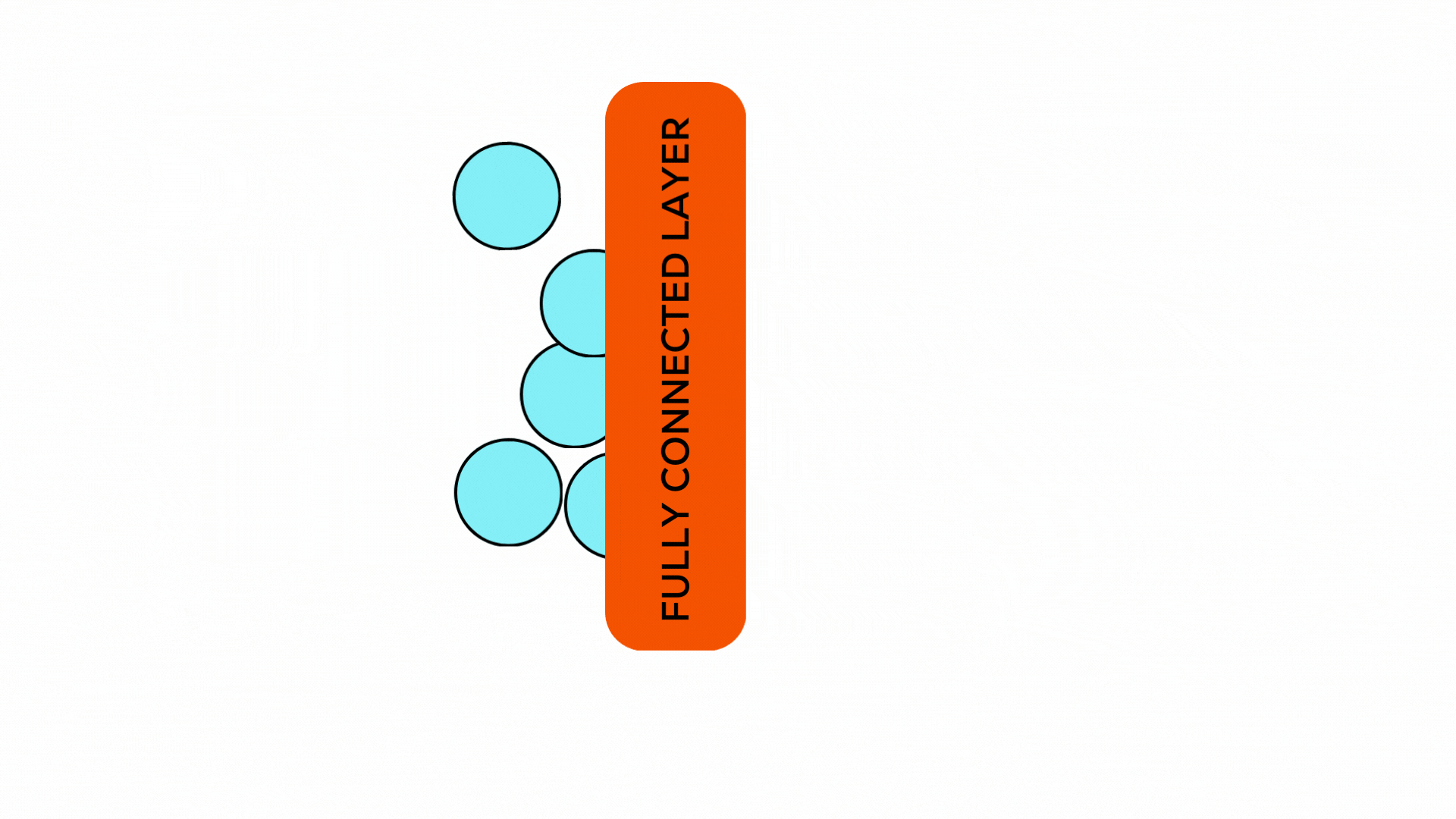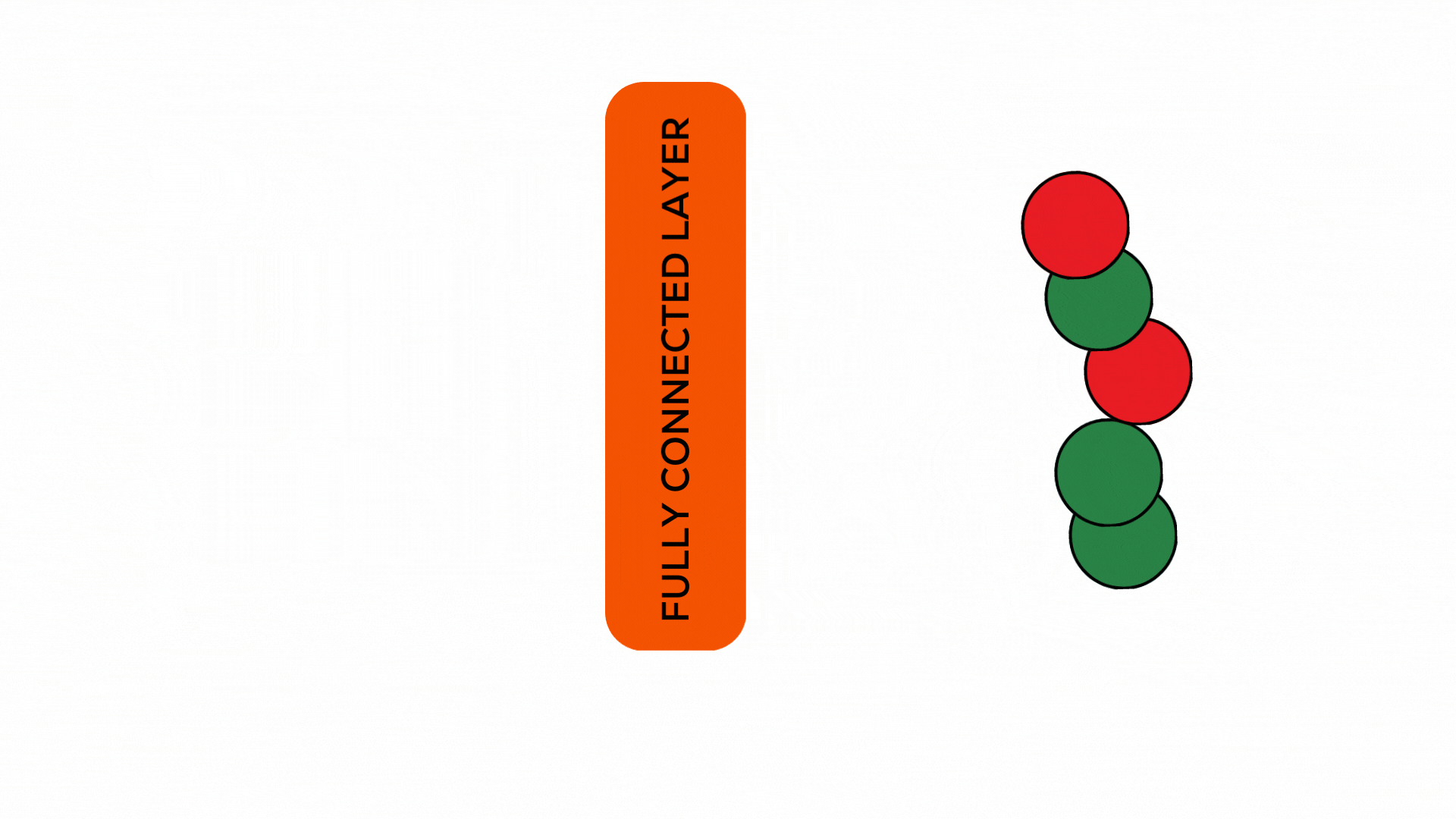
Figure 3: Illustration of the graph readout phase where nodes are collected for the final classification tasks.
After multiple rounds of message passing, the GNN performs a readout phase:
- The final hidden states of nodes are collected.
- A learnable readout function processes these states and produces the final output of the GNN model.
This architecture makes GNNs particularly well-suited for network security applications, where understanding the relationships between different network components is crucial for detecting anomalies and potential threats.
Why GNNs are Superior to Traditional Neural Networks for Network Security?
GNNs offer several key advantages over traditional neural networks when handling network security challenges:
Natural Network Representation
- Traditional neural networks struggle to process variable-size network data and often require complex preprocessing to handle network traffic. This frequently leads to loss of important structural information.
- GNNs use a native graph structure that perfectly mirrors real network topologies. Each network device becomes a node, and communications between devices are represented as edges, preserving the entire network structure.
- The ability to model both hosts and traffic flows as interconnected entities allows GNNs to maintain and analyze complete network contexts. This help capturing subtle patterns that might indicate an attack.
Relationship Learning
- Traditional neural networks process data points in isolation, making it difficult to identify coordinated attacks that involve multiple network components.
- GNNs excel at capturing complex dependencies between network entities through their message-passing mechanism. This allows them to understand how different parts of the network influence each other.
- By analyzing relationships between hosts, traffic patterns, and network behaviors, GNNs can better detect sophisticated attack patterns that might appear normal when examining individual components in isolation.
Task Versatility
- Traditional neural networks typically focus on simple classification tasks and struggle with multi-level analysis of network behavior.
- GNNs can simultaneously perform analysis at multiple levels:
- Node-level analysis: Detecting suspicious behavior of individual hosts.
- Edge-level analysis: Identifying abnormal communication patterns between devices.
- Graph-level analysis: Understanding overall network health and detecting system-wide attacks.
- This multi-level capability allows for more comprehensive security monitoring and more accurate threat detection.
Enhanced Interpretability
- Traditional neural networks often operate as black boxes, making it difficult to understand why certain traffic was flagged as malicious.
- GNNs can provide clearer insights into their decision-making process by revealing:
- Which nodes (devices) and connections played crucial roles in detecting an attack.
- The specific patterns in network traffic that triggered alerts.
- How attacks propagate through the network.
- This interpretability is crucial for security teams who need to understand and respond to threats quickly and effectively.
Approaches to DDoS Detection Using Graph Neural Networks
Recent research has introduced two primary approaches to applying GNNs for DDoS attack detection: Flow-based and Packet-based, each with its own unique advantages and considerations. Let's dive deep into these approaches.
Packet-Based Approach
The application of GNNs to packet-level analysis for DDoS detection has been an active area of research, with multiple approaches proposed by researchers. GoGDDoS introduced a multi-classifier approach using a graph-of-graph structure to capture relationships between packets and flows. FTG-Net proposed a hierarchical flow-to-traffic graph representation that combines both traffic-level and flow-level relationships.In the context of Software-Defined Networking, researchers have explored spatial-temporal graph convolutional networks for both detection and mitigation of DDoS attacks.
In this article, we'll focus on one particularly effective approach: GraphDDoS, developed by Li et al. Their packet-based methodology offers a framework for transforming network traffic into a temporal graph structure, demonstrating impressive results in attack detection. Let's examine how this approach works in detail.
How graph is constructed?
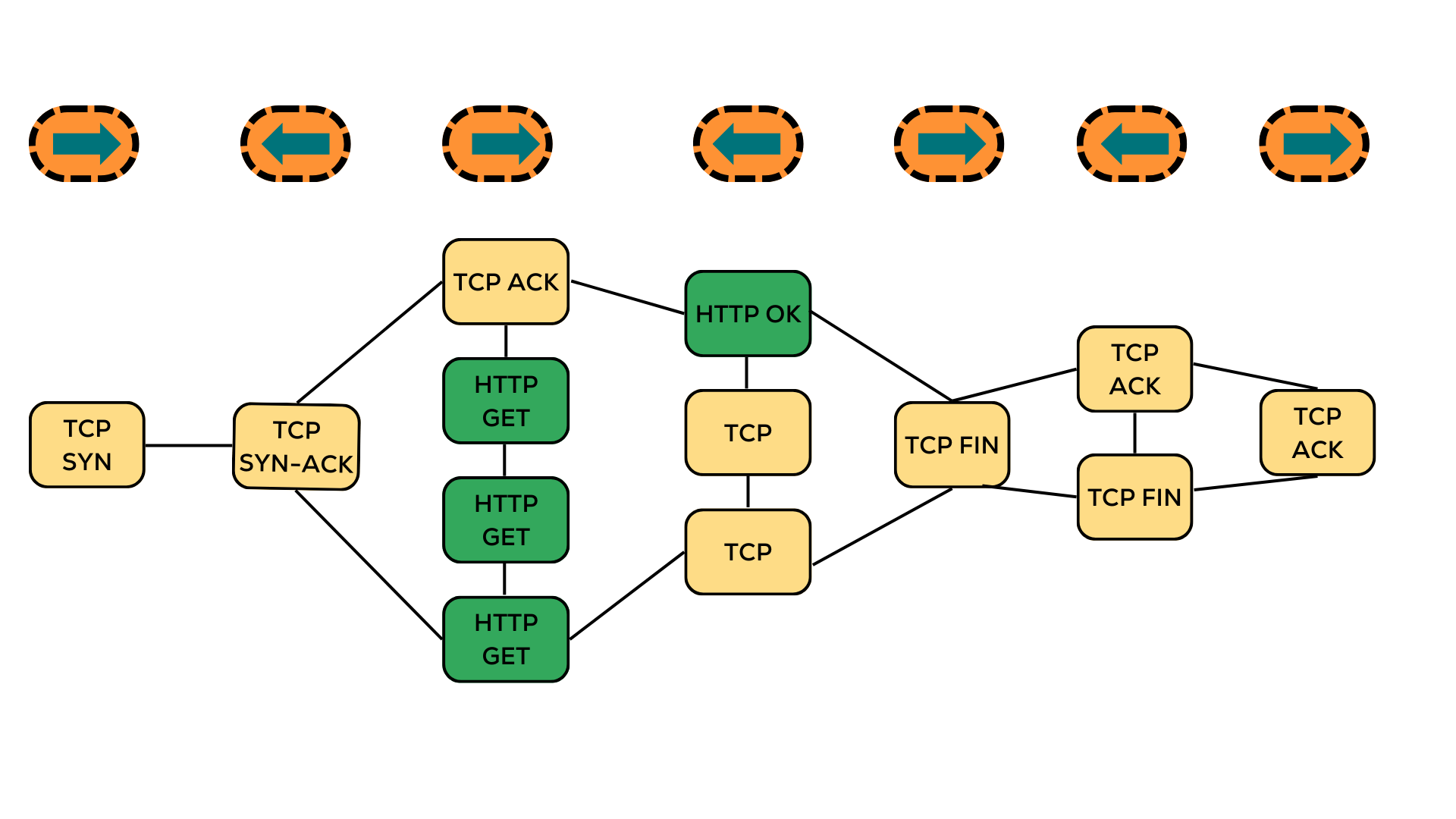
Figure 4:The figure illustrates how packets are organized and connected based on their temporal and spatial relationships.
- Packet Organization
- Packets are initially grouped by source and destination IP addresses.
- Temporal ordering is maintained by sorting packets based on timestamps.
- A predefined maximum number of packets is considered to maintain computational efficiency.
- Node Creation
- Each packet becomes a node in the graph.
- There is only one node feature: Protocol type (TCP, UDP, HTTP).
- Edge Definition
- Two types of connections are established:
- Sequential edges: Between consecutive packets traveling in the same direction
- Cross-directional edges: Linking the last packet of one direction to the first packet of the opposite direction
- Two types of connections are established:
The Learning Process
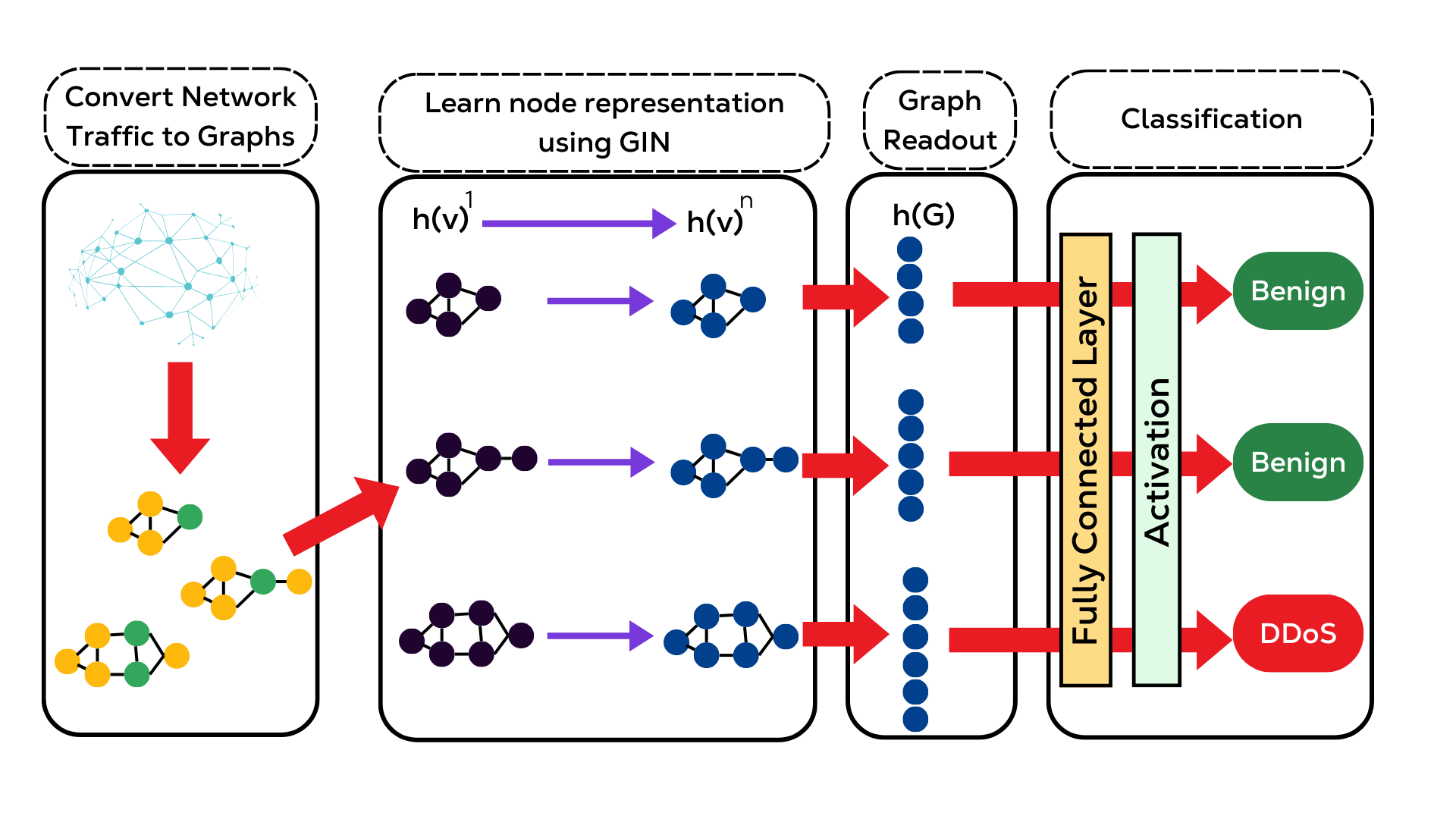
Figure 5: Detailed overview of the GraphDDoS learning process, showcasing the four-stage architecture from initial packet processing to final attack classification.
The GNN model employs a systematic four-stage architecture that progressively transforms raw network data into actionable security insights:
- Traffic-to-Graph Conversion Stage
The model begins by transforming network data into structured graph representations as described in the previous section.
- Node Representation Learning with Graph Isomorphism Network (GIN)
The Graph Isomorphism Network (GIN) layer serves as the foundation for learning sophisticated node representations that capture both local and global packet interaction patterns. Here's how it works:
Message Passing Phase
For each node v in the graph, GIN updates its representation through iterative message passing:
$h_v^{k+1} = MLP((1 + ε)h_v^k + ∑_{u∈N(v)} h_u^k)$
Where:
- $h_v^k$ represents node v's features at iteration k
- $N(v)$ represents the neighbors of node v
- $ε$ is a learnable parameter
- MLP is a multi-layer perceptron
This process:
- Combines information from the node itself with aggregated neighbor information.
- Preserves both node features and structural information.
- Updates representations over multiple iterations to capture increasingly complex patterns.
The GIN's unique architecture ensures that distinct network structures lead to different representations, making it particularly effective at identifying anomalous traffic patterns indicative of DDoS attacks.
- Graph-Level Information Aggregation
After developing rich node representations, the model performs graph readout:- Consolidates individual node features into a comprehensive graph embedding.
- Employs sophisticated pooling strategies to preserve critical information.
- Creates a fixed-size representation regardless of network size.
- Captures global patterns across the entire network structure.
- Final Classification Stage
The classification process involves:- Processing the graph-level embedding through fully connected layers.
- Applying non-linear transformations to capture complex patterns.
- Making final classifications based on learned thresholds.
Results on important baseline datasets
The effectiveness of this packet-based approach has been validated through extensive experimentation on standard network security datasets such as CIC-IDS2017 and CIC-DOS2017:
- On the CIC-IDS2017 dataset, the model achieved exceptional performance with 99.59% accuracy and 99.59% F1 score, along with precision of 99.65% and recall of 99.53%.
- Testing on the CIC-DOS2017 dataset showed robust performance with 97.51% accuracy and 94.56% F1 score, supported by 95.05% precision and 94.07% recall.
Flow-Based Approach
The application of Graph Neural Networks to flow-level analysis has emerged as a promising direction in network security research, with several approaches proposed in recent literature. Researchers have explored diverse methodologies: ARGANIDS introduced an adversarially regularized graph autoencoder for unsupervised learning from network flows, E-GraphSAGE detects intrusion in IoT networks by effectively modeling flows as edges, and Anomal-E introduces a self-supervised edge-centric approach for anomaly detection.
In this section, we'll examine the methodology presented in "Unveiling the Potential of Graph Neural Networks for Robust Intrusion Detection" by Pujol-Perich et al. Their approach stands out for its treatment of network flows and host relationships, offering a framework that has demonstrated exceptional performance in DDoS attack detection.
How graph is constructed?
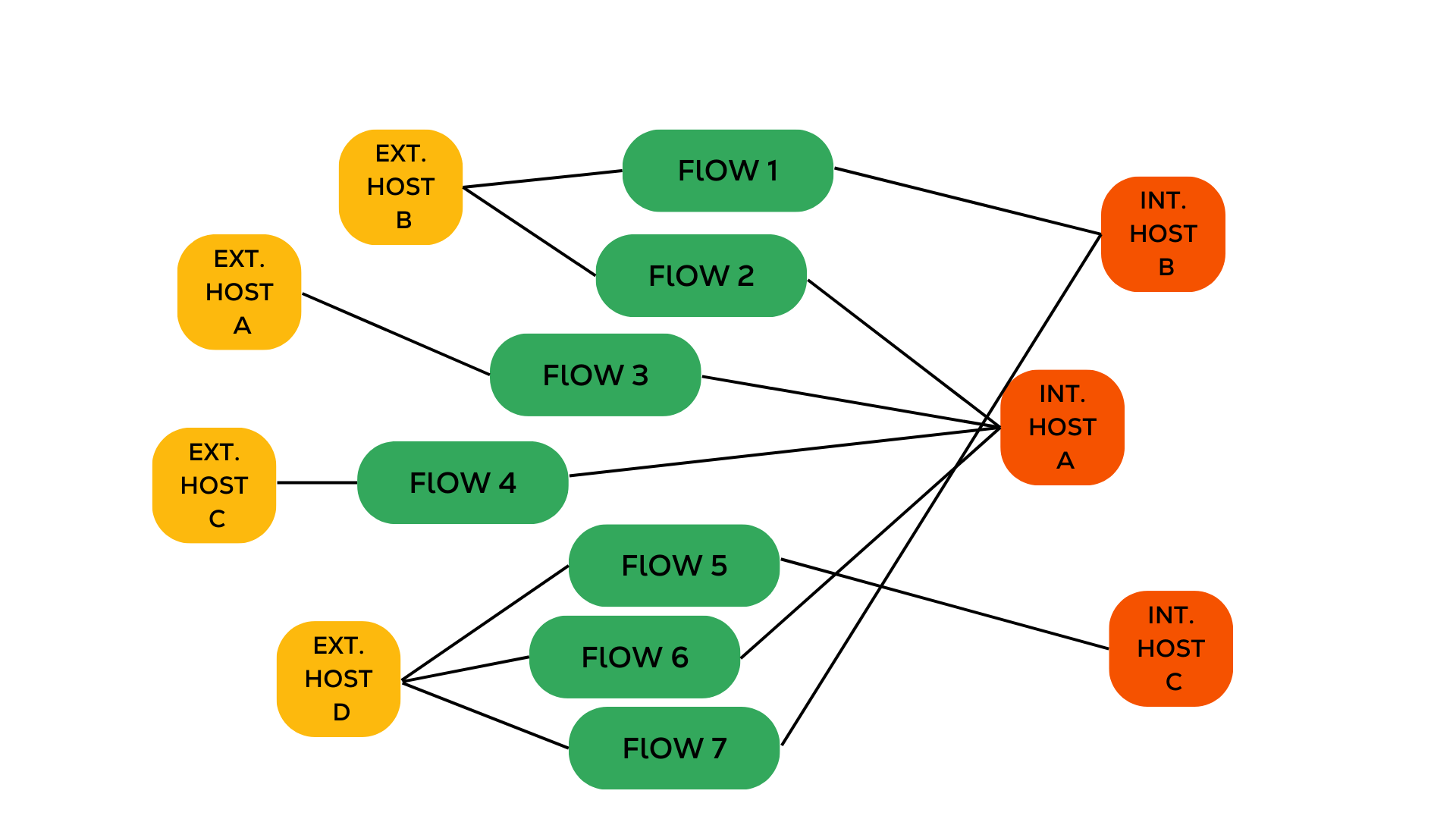
Figure 6: Host-Connection graph structure used in GraphRNIDS, demonstrating the dual-node type approach with host nodes and flow nodes, connected through edges representing network communications.
- Dual Node Types
- Host nodes: Represent source and destination IPs
- Flow nodes: Represent individual network flows
- Feature Engineering
- Flow nodes have with features including:
- Packet size statistics
- Flow duration
- Protocol information
- Traffic patterns
- Host nodes are initialized with uniform values, learning richer representations through message passing
- Flow nodes have with features including:
- Edge Relationships
- Source-to-flow edges: Connecting source hosts to their initiated flows
- Flow-to-destination edges: Linking flows to their target hosts
The Learning Process
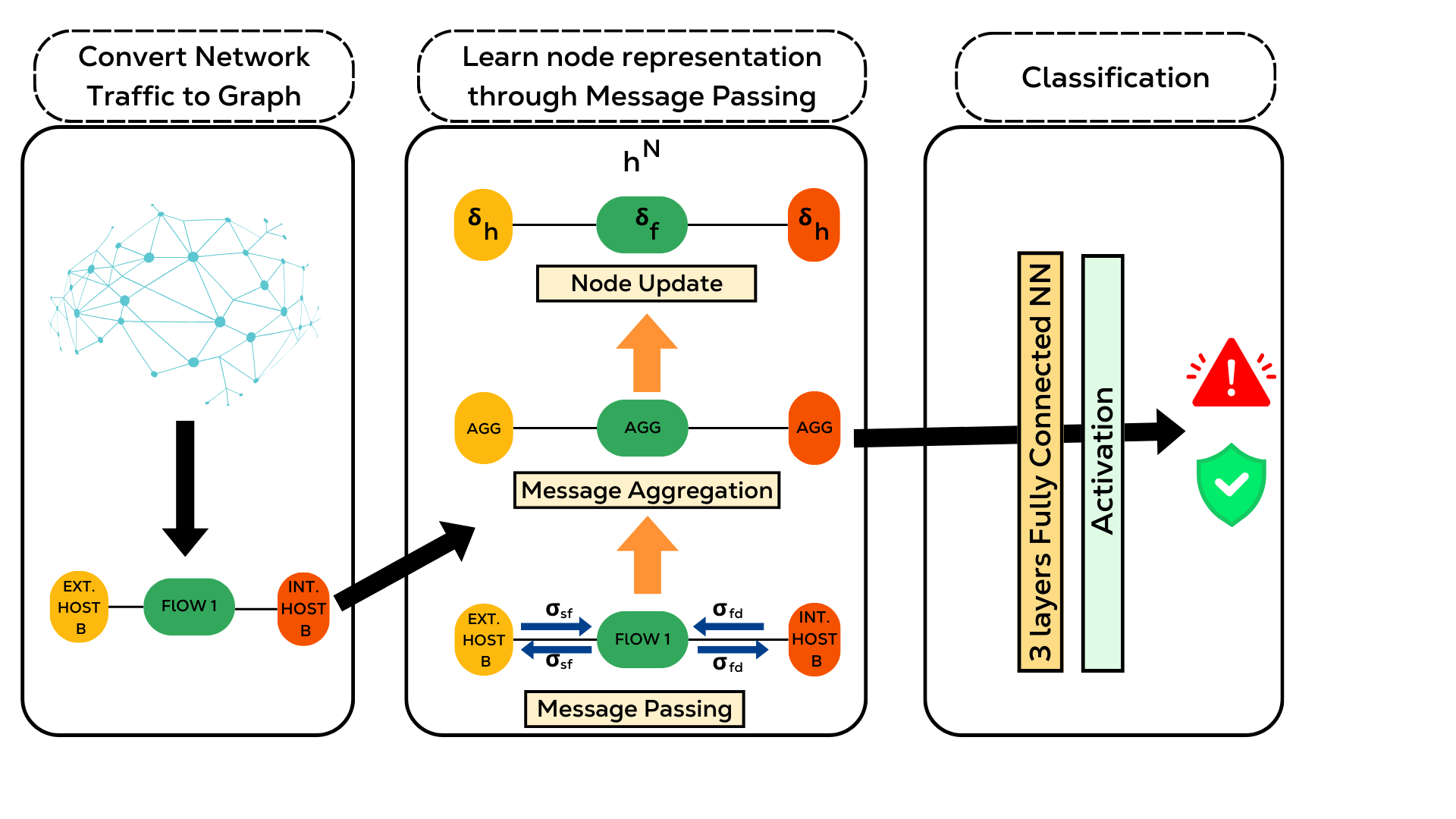
Figure 7: Complete architecture of the GNN-based Network Intrusion Detection System (NIDS), showing the flow of information through various processing stages from input to final classification.
The GNN model uses a three-stage pipeline for attack detection:
- Network Traffic Graph Construction
The initial stage transforms raw traffic data into a heterogeneous graph structure as described above.
- Message Passing Framework
The key components of this framework include:
- Specialized Message Functions
- Host-to-flow ($σ_{sf}$) messages capture source behavior.
- Flow-to-host ($σ_{fd}$) messages encode destination patterns.
- Both message functions are implemented as 2-layer neural networks.
- Message Aggregation Strategy
- Uses element-wise mean aggregation over computed messages for each node.
- This choice provides better normalization of data across multiple message-passing iterations.
- Offers improved stability compared to traditional element-wise summation approaches.
- State Updates via GRUs
- Processes aggregated messages and current node states through specialized update functions.
- Employs two distinct learnable functions: $δ_h$ for host nodes and $δ_f$ for flow nodes.
- Updates node hidden states independently based on their type (host or flow), enabling the model to learn different patterns for each.
- Specialized Message Functions
- Multi-Layer Classification
The final stage employs the following classification network:
- Implements a three-layer fully connected neural network that processes final hidden states of flows.
- Uses ReLU activation for first two layers and softmax activation for the output layer.
Results on important baseline datasets
The effectiveness of this flow-based approach has been evaluated on CIC-IDS2017 dataset:
- The model achieved an accuracy greater than 99% accuracy against the DDoS attack class.
Future Implications and Challenges
While GNN-based approaches for DDoS detection show remarkable promise, several key challenges and opportunities need attention:
Technical Challenges
- Computational Complexity: As networks grow in size and complexity, processing large-scale graph structures in real-time becomes increasingly demanding. Future research needs to focus on optimization techniques and efficient implementations for handling enterprise-scale networks.
- Model Interpretability: While GNNs provide better interpretability than traditional neural networks, there's still room for improvement in helping security analysts understand why specific traffic patterns are flagged as attacks.
- Adversarial Vulnerabilities: GNN-based detection systems may be susceptible to
adversarial attacks where malicious actors deliberately manipulate network traffic patterns to
evade detection. For example:
- Attackers could modify their traffic patterns to create graph structures that the model classifies as benign.
- Strategic changes in packet timing or flow characteristics could disrupt the graph's structural properties.
- Poisoning attacks during model training could compromise detection accuracy.
Future Research Directions
- Dynamic Graph Learning: Developing methods to handle temporal aspects of network traffic more effectively, allowing models to adapt to evolving attack patterns in real-time.
- Adversarial Robustness: Investigating techniques to make GNN models more
resilient against adversarial attacks, such as:
- Robust training methods that consider potential graph perturbations.
- Detection mechanisms for identifying manipulated traffic patterns.
- Hybrid Approaches: Exploring combinations of GNN-based detection with traditional security measures to create more robust defense systems.
- Transfer Learning: Investigating how models trained on one network environment can be effectively adapted to others, reducing the need for extensive retraining.
Conclusion
The application of Graph Neural Networks to DDoS attack detection represents a significant advancement in network security. Through both packet-based and flow-based approaches, GNNs have demonstrated their ability to capture complex network relationships and identify attack patterns with remarkable accuracy.
The key advantages of these approaches include:
- Superior pattern recognition through graph-based learning.
- Ability to capture both local and global network behaviors.
- Robust performance across different types of DDoS attacks.
- Adaptability to varying network sizes and configurations
As cyber threats continue to evolve, GNN-based approaches offer a promising foundation for next-generation security systems. Their ability to learn from network structure and adapt to new patterns positions them as an important tool in the ongoing battle against DDoS attacks.