
Kartikeya Sharma
CyberSecurity and AI 🤖
Developed reporting tools and analytical dashboards to standardize processes and increase understanding of cybersecurity threats. Managed the implementation of a new cybersecurity tool, ensuring data accuracy and leading training sessions to improve security practices.
Python
JavaScript
Flask
Elasticsearch
PyTorch
DGL
Pandas
NumPy
Matplotlib
SciPy
Apache ECharts
Developed lab materials and conducted demonstrations in C for the CS 415 Operating Systems course. Led weekly lab sessions and provided dedicated office hours to assist students with assignments and exam preparations.
Developed applications and interfaces to enhance payment processes, user experience, and financial management, improving operational efficiency and data integrity.
Python
JavaScript
SQL
Bash
Flask
MySQL
SQLite
Pandas
NumPy
Guided students through class projects and assisted in creating, reviewing, and grading assignments while holding office hours to support student learning for the CS 422 Software Method I course.
Developed data processing tools and contributed to cybersecurity analytics pipelines to enhance threat detection capabilities.
Python
JavaScript
Bash
Flask
Elasticsearch
Pandas
NumPy
Matplotlib
SciPy
Developed Graph Neural Networks for spam detection in social networks. Contributed to a distributed system to accelerate training on large-scale graphs.
Developed web applications, machine learning models, and data analysis solutions to streamline processes, automate tasks, and support decision-making. Managed databases, cloud deployments, and explored new technologies for continuous improvement.
Python
JavaScript
SQL
Bash
Flask
Django
MySQL
SQL Server
SQLite
AWS
Scikit-learn
NLTK
Pandas
NumPy
Matplotlib
Developed applications for optimizing shipment hub locations, standardizing SKU data, streamlining inventory counting, and automating invoice validation to improve operational processes.
Python
JavaScript
SQL
Bash
Flask
MySQL
SQLite
Pandas
NumPy
Matplotlib
GeoPandas
Leaflet.js
Developed teaching materials, taught weekly classes, created and graded assignments and exams, and arranged guest lectures for COSC 375, Machine Learning course.
Mined unstructured text data from PDF files, defined and analyzed KPIs, and developed and distributed reports to support data-driven decision making.
Python
SQL
PyQT
SQL Server
PyPDF2
Pandas
Matplotlib
Power BI
SSRS
Python
SQL
SQL Server
Pandas
Power BI
Microsoft Excel
Developed a distributed geo-spatial version of Schelling’s model of segregation to overcome computational constraints. Employed Morton and Geohash partitioning techniques to optimize computational efficiency and evenly balance workloads. Achieved up to 17 times speedup and demonstrated excellent horizontal scalability in simulations involving millions of agents.
Developed Logistic Regression models to predict NCAA Division 1 Men’s Tennis Nationals outcomes, demonstrating the effective use of machine learning in sports analytics. The Logistic Regression (Backward Selection AIC) model achieved the highest accuracy of 84.07% and the top F-1 score.
Developed a Graph Neural ODE model for Twitter spam detection using various ODE solvers, including Euler, Runge-Kutta, and Adams. Achieved significantly faster training and inference times compared to traditional methods, although the accuracy was slightly lower. This approach addresses the challenges of training on large graph datasets by using efficient numerical methods for computation and parameter management.
Developed a Real-time Heterogeneous Graph Neural Network (RHGNN) model for Twitter spam detection, using Graph Attention Networks and Semantic Attention networks. Achieved significantly faster training and inference times compared to traditional methods, with GPU training speeding up by 168 times and inference by 74 times, but with a slightly lower accuracy. This approach addresses the challenges of training on large, heterogeneous graph datasets, making it a viable candidate for real-time spam detection.
Explored the critical role of data analytics in contemporary accounting. Built a Flask (Python) web application demonstrating the superior efficiency of big data analytics compared to traditional tools like Microsoft Excel, particularly in auditing processes.
Utilized geospatial simulations of Schelling's segregation model to assess racial majorities' tolerance towards minorities in specific U.S. states. Selected for presentation at the Goshen College Annual Academic Research Symposium, 2019.
Applied the Gale-Shapley Algorithm to find the best stable matches between Resident Assistant applicants and respective floors. Conducted sensitivity analyses on over a million preference orders to determine the most likely matches.
Created an innovative Android application that serves as a remote control for an Arduino-based car, combining mobility with advanced technology.
Built a Cost of Goods Sold (COGS) calculator using Flask for Goshen College's coffee shop, Java Junction. The tool simplified expense calculations, improving operational efficiency.
Compared various Python-based linear regression methods, evaluating their performance speed and results. Focused on analyzing the relationship between India's annual Foreign Export data and Gross Domestic Product.
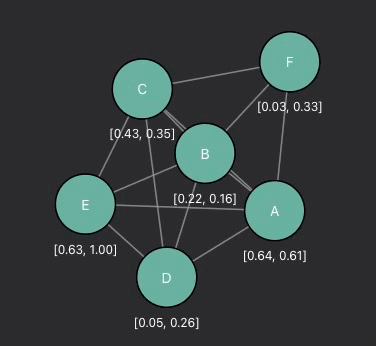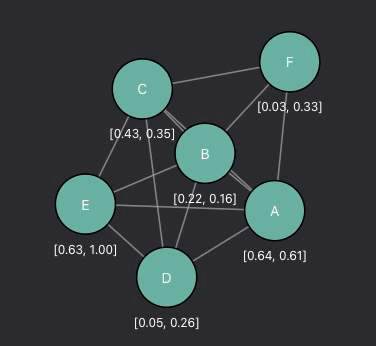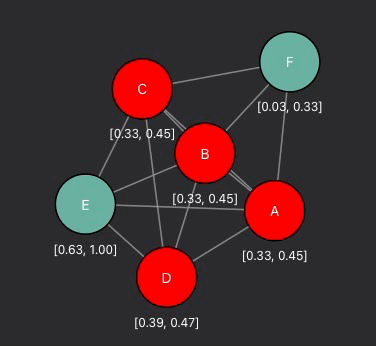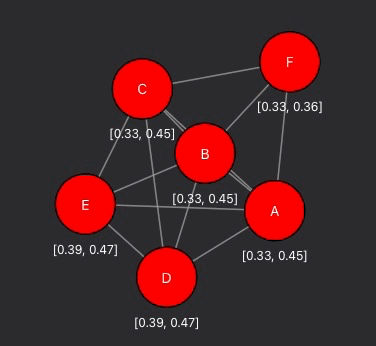
This project visualizes the message passing and feature aggregation processes within Graph Neural Networks (GNNs). By providing an intuitive, step-by-step demonstration of how node features are combined and updated, it helps users better understand the inner workings of GNNs and the mathematics behind feature aggregation.
This project evaluates the application of Schelling’s Model of segregation in real-world geographical scenarios using a distributed system. The project optimizes computational efficiency through advanced partitioning techniques and a master-worker architecture. The distributed system significantly outperforms centralized approaches, achieving up to 17 times faster performance in large-scale simulations involving millions of agents. The system also shows excellent horizontal scalability, maintaining consistent performance as the number of processes increases.
Python
Pandas
NumPy
GeoPandas
Matplotlib
SciPy
MPI4Py
Dask

This project utilizes the Indian Government's CoWin API to create an automated script that notifies people when a vaccine is available in their district. The script continuously checks for vaccine availability and sends alerts to users, ensuring they stay informed about vaccination slots in real-time.
This project optimizes the matching of Resident Assistants to floors using the
Gale-Shapley algorithm. The main goal of the project is to find a stable matching for
two
asymmetric arrays: students applying for Resident Assistant (R.A.) jobs and the number
of available R.A. jobs. Each job is assigned a personality trait, and candidates are
given preferences accordingly. The Gale-Shapley algorithm is applied to achieve an
optimal and stable matching, which is validated through sensitivity analysis.
The findings show that there is only one stable matching, guaranteeing an optimal
allocation
of Resident Assistant positions. The sensitivity analysis further supports the
robustness of the matching algorithm, highlighting that changes in preferences have a
minimal impact on the stability of the results. This project offering insights into
effective
resource allocation in scenarios with more applicants than available positions.
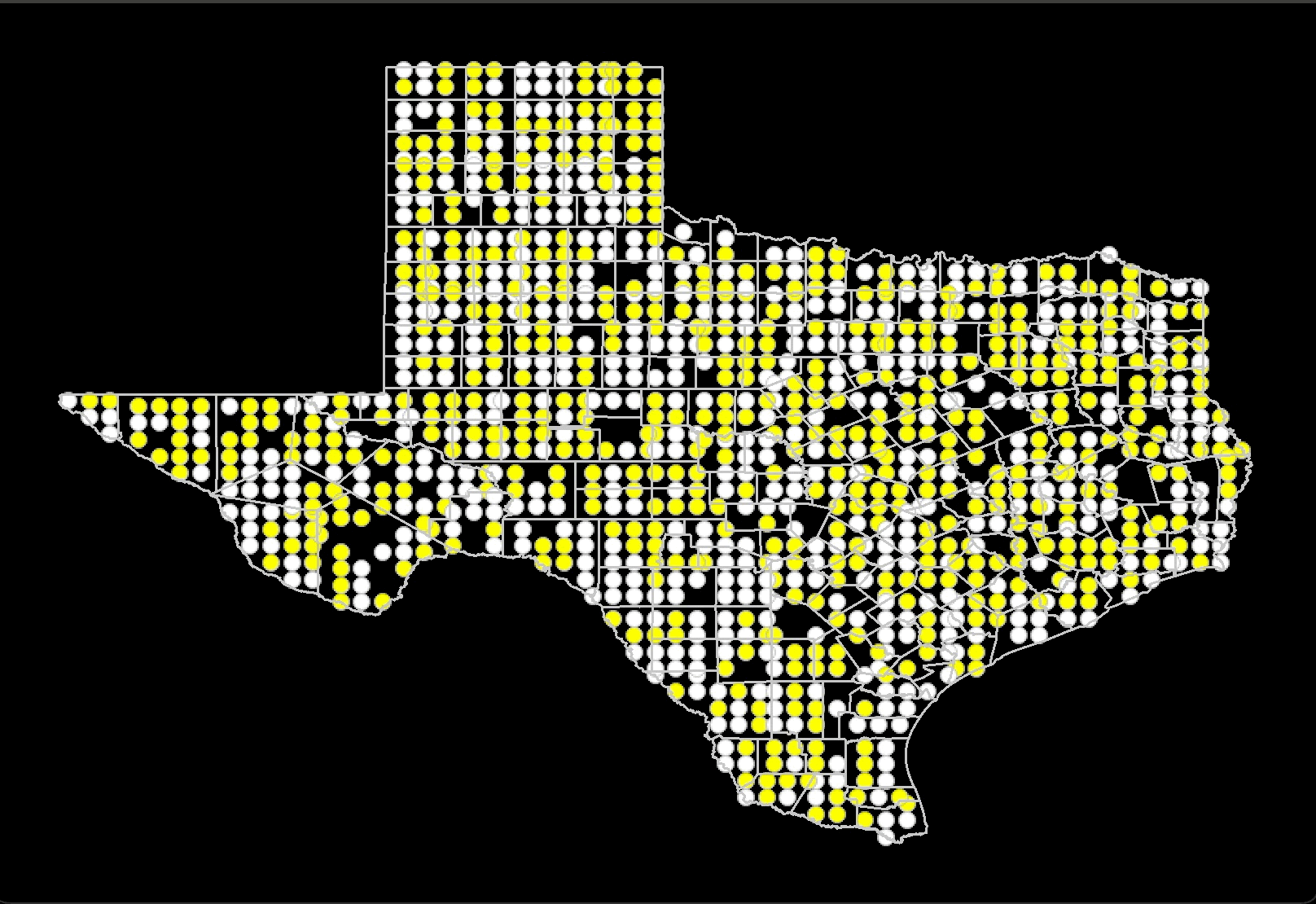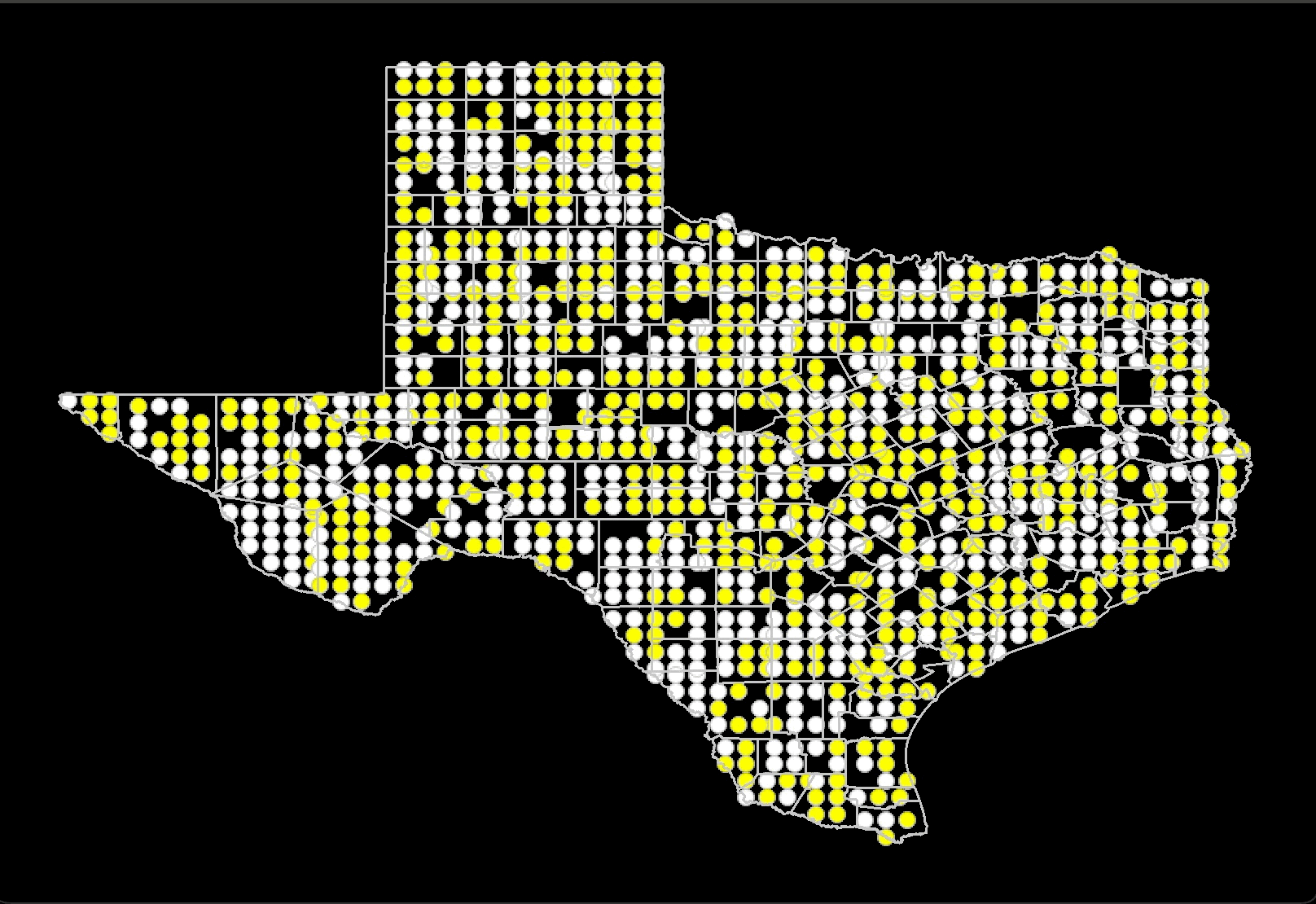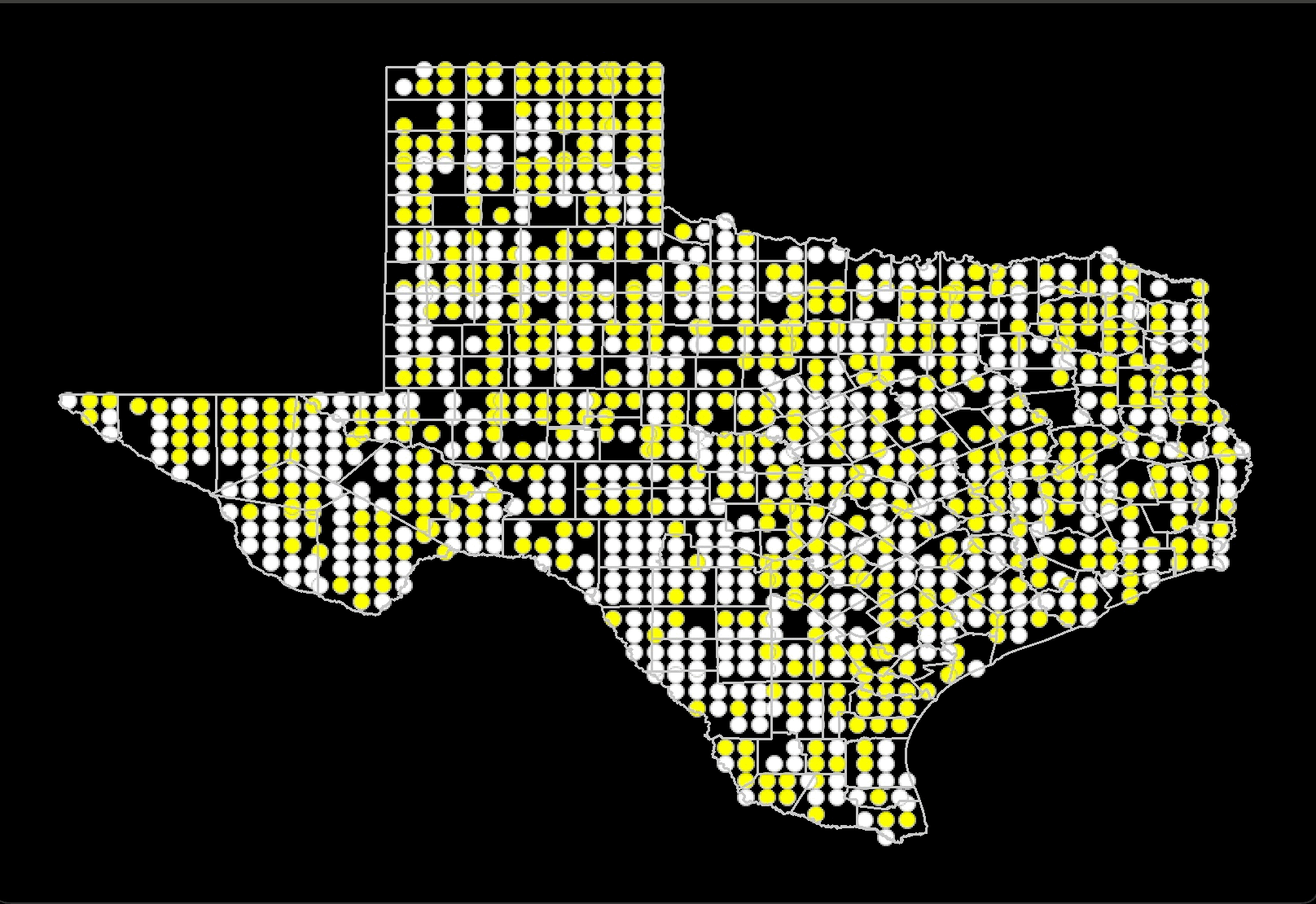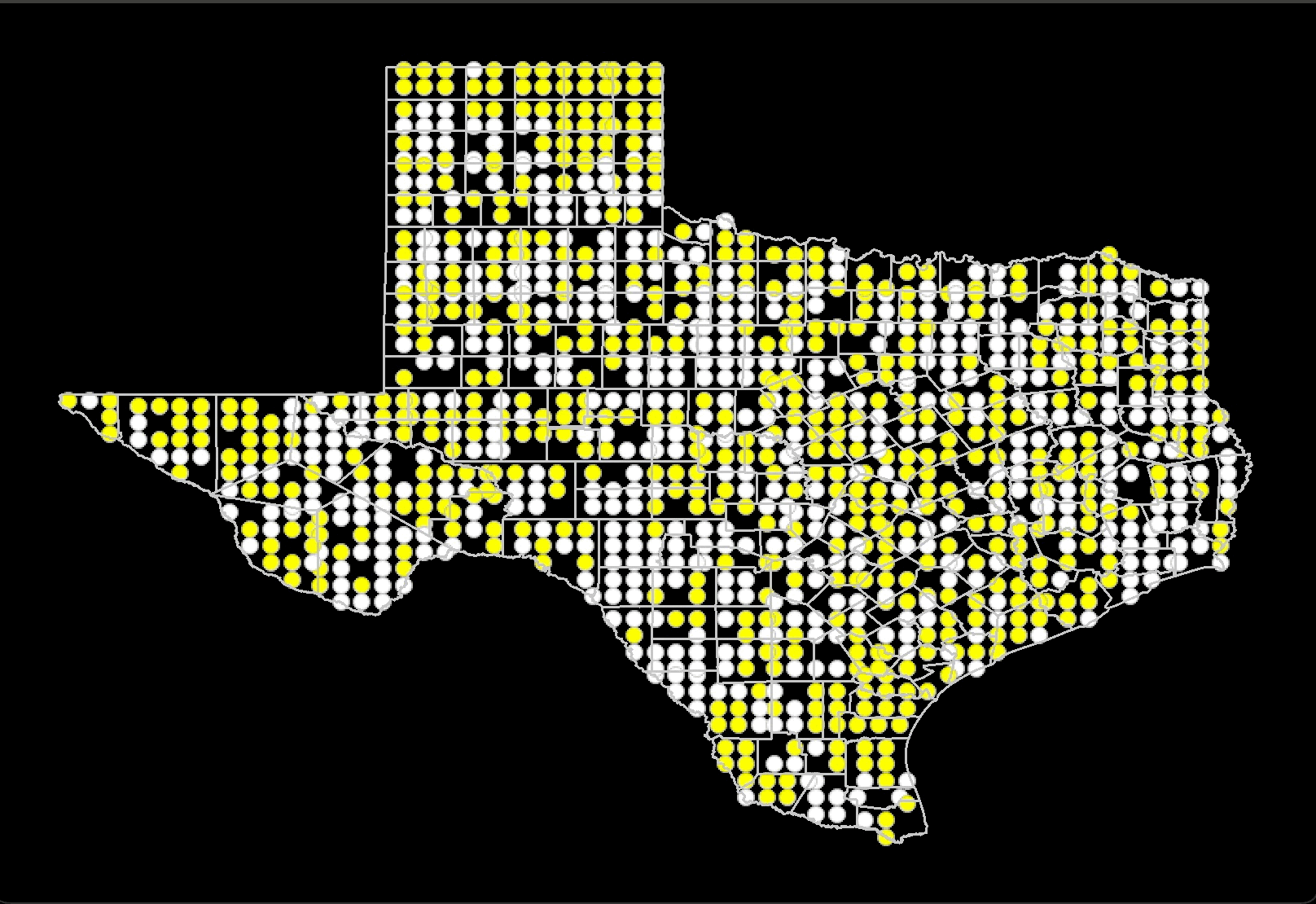
This project evaluates racial tolerance across American states using a geospatial
version of Schelling’s Model of segregation. By simulating the distribution of ethnic
groups within states, the project analyzes the relationship between desired and actual
similarity among neighbors. Census data on racial diversity
by county is used to run these simulations, which are then compared with real-world data
through visual inspection and statistical tests like the Kolmogorov-Smirnov test.
The findings show that states with lower similarity thresholds, indicating higher
tolerance, often correspond with states identified as more liberal or tolerant in
existing research and rankings. Moreover, the study shows that while higher similarity
thresholds can increase segregation but very high thresholds can paradoxically lead to a
multicultural society. This project offers a quantifiable measure of state-level
tolerance and insights into the dynamics of ethnic distribution and
social cohesion within states.
In this article, we explore how Graph Neural Networks (GNNs) can improve the detection of Distributed Denial of Service (DDoS) attacks in network security. We examine GNNs' unique ability to process and learn from graph-structured network data, making them particularly effective for identifying complex attack patterns. The article details two primary approaches: a packet-based method that analyzes individual network packets as graph nodes, and a flow-based method that considers broader traffic patterns. GNNs' advanced architectural capabilities enhance detection accuracy and also provide security teams with interpretable insights into attack patterns, paving the way for more robust and adaptive network defense systems in an increasingly complex threat landscape.
In this talk, we explore how large language models like ChatGPT can be transformed from perceived cybersecurity threats into powerful allies for strengthening organizational security posture. We'll demonstrate how security engineers of all coding skill levels can leverage GPT and embedding APIs to build three key systems: an intelligent semantic matching system for pattern recognition, an application anomaly detection system for monitoring employee workstations, and a threat intelligence correlation platform that generates actionable insights from multiple sources. The presentation covers practical implementation strategies, the synergistic use of embedding and chat APIs, real-world applications, and ethical considerations for integrating AI into security operations.
Not Available
In this talk, we explore how insider threats pose significant risks to organizational security by evading traditional detection methods. Graph Neural Networks (GNNs) offer an innovative solution by modeling users, devices, and activities as interconnected nodes and edges in a graph structure, effectively capturing complex relationships and behavioral patterns. Research shows that GNN-based models demonstrate superior performance compared to conventional machine learning techniques in identifying insider threats. The exploration of various GNN architectures and their real-world applications provides valuable insights for cybersecurity professionals seeking to enhance organizational security against insider threats.
Coming Soon
In this talk, we will explore the application of Graph Neural Networks (GNNs) in detecting Distributed Denial of Service (DDoS) attacks. We will introduce GNNs, compare them with traditional neural networks, and highlight their evolution and adoption. We will also compare traditional detection methods with AI-based approaches and how GNN based approaches can be advantageous. Finally, we will talk about two important GNN models used in DDoS detection and discuss their superior performance compared to traditional machine learning models.
Coming Soon
In this talk, we will explore the application of Graph Neural Networks (GNNs) in detecting Distributed Denial of Service (DDoS) attacks. We will introduce GNNs, compare them with traditional neural networks, and highlight their evolution and adoption. We will also compare traditional detection methods with AI-based approaches and how GNN based approaches can be advantageous. Finally, we will talk about two important GNN models used in DDoS detection and discuss their superior performance compared to traditional machine learning models.
Coming Soon
In this talk, I will present my research on the cutting-edge world of Graph Neural Networks (GNN) and their transformative role in combating one of the most prevalent cyber threats: DDoS (Distributed Denial of Service) attacks. I will uncover how GNNs offer a significant advancement over traditional methods of detection, delving into the evolution of GNNs and exploring their unique application in cybersecurity. We'll close with a forward-looking view on how the advancements in GNNs are equipping us with better shields in the digital arena against DDoS threats.
Not Available